Terraform Introduction
Infrastructure as a Code (IaC):
So, what is IaC? It's just a fancy made-up term for deploying and controlling the cloud infrastructure as a series of configuration files instead of using the GUI and the most popular IaC tool is Terraform.
Terraform is a program written in the 'Go' language that lets us deploy infrastructure on different platforms using plugins called providers. Providers let us perform CRUD (Post Get Put Delete) operations on the Target APIs as depicted below:
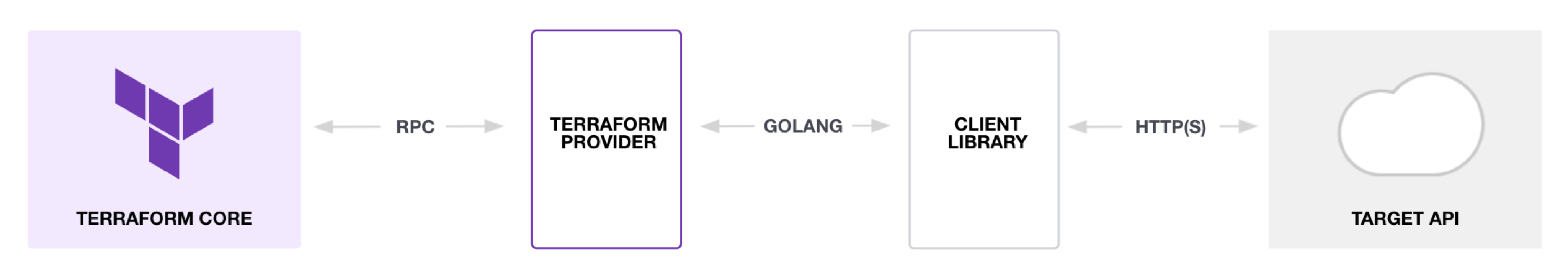 |
| Figure [1] Terraform calls |
We write Terraform scripts in a Terraform Domain-Specific language called 'Hashicorp Configuration Language' (HCL).
We will now have a '.terraform' directory with the 'aws' provider downloaded into it and also a '.terraform.lock.hcl' file that specifies the exact provider version used.
After applying the configuration, terraform keeps a record of the infrastructure in a file named 'terraform.tfstate', terraform does this so the resources deployed with Terraform can be updated or destroyed easily in the future. The best practice in production is to copy the state file to a remote location (such as an S3 bucket). To inspect the current state, we can run a 'terraform show' command.
We can list all the Terraform resources using the 'terraform state list' command. Once we're done with our environment, we can easily terminate all the resources we deployed with the 'terraform destroy' command.
Working with Terraform and AWS:
Terraform lets you declare infrastructure in a Declarative manner. Modules are reusable Terraform configurations that may contain one or more providers.
Step 1 - Install Terraform (we will only cover RHEL 8 here for the sake of brevity):
sudo yum install -y yum-utilssudo yum-config-manager --add-repo https://rpm.releases.hashicorp.com/RHEL/hashicorp.reposudo yum -y install terraform
Step 2 - Using the AWS provider:
One of the first steps to using the AWS provider is to set up the Authentication and Configuration, the following are the methods of setting up Authentication:
- Parameters in the provider configuration
- Environment variables
- Shared credentials files
- Shared configuration files
- Container credentials
- Instance profile credentials and region
Let's go for the easiest option, 'Parameters in the provider configuration', and explore more secure options at a later time.
On our machine, let's create a new directory, and create a 'main.tf' file with the following code in it. Please replace the "my-access-key" and "my-secret-key" with your account credentials.
terraform {required_providers {aws = {source = "hashicorp/aws"version = "~> 4.16"}}required_version = ">= 1.2.0"}provider "aws" {region = "us-west-2"access_key = "my-access-key"secret_key = "my-secret-key"}resource "aws_instance" "app_server" {ami = "ami-830c94e3"instance_type = "t2.micro"tags = {Name = "ExampleAppServerInstance"}}
Our code above is organized into blocks, viz. 'terraform', 'provider', & 'resource' blocks. In the resource block, the type of resource is 'aws_instance' and the name of the block is 'app_server'.
Let's now initialize the terraform directory by running 'terraform init' command. The result of which should look as follows:
 |
| Figure [2] Terraform init |
We will now have a '.terraform' directory with the 'aws' provider downloaded into it and also a '.terraform.lock.hcl' file that specifies the exact provider version used.
We will now run 'terraform fmt' & 'terraform validate' commands to automatically update all Terraform configuration files in the current directory to uniform formatting and perform the validation process ensuring that the configurations are syntactically valid. Following this, we will run the 'terraform plan' command that will let us preview changes that Terraform would make to our infrastructure.
After reviewing the plan, we can run 'terraform apply' to run the infrastructure. It will once again show us the plan and we can type in 'yes' to proceed.
 |
| Figure [3] Terraform apply |
After applying the configuration, terraform keeps a record of the infrastructure in a file named 'terraform.tfstate', terraform does this so the resources deployed with Terraform can be updated or destroyed easily in the future. The best practice in production is to copy the state file to a remote location (such as an S3 bucket). To inspect the current state, we can run a 'terraform show' command.
 |
| Figure [4] Terraform show |
We can list all the Terraform resources using the 'terraform state list' command. Once we're done with our environment, we can easily terminate all the resources we deployed with the 'terraform destroy' command.
We will discuss changing infrastructure, input variables, querying data with outputs, & storing state remotely in another post. Thank you for reading! :D
---
References:
[1] Terraform AWS provider - https://registry.terraform.io/providers/hashicorp/aws/latest/docs#assuming-an-iam-role


Comments
Post a Comment